It was the time of early 2012 when anonymous social media applications entered the market. Applications like Yik Yak gained popularity in just new month's where privacy played a significant role. People who are active on social media pages ask for a higher degree of confidentiality and privacy, and this is what anonymous social media applications brought to them! Let's face it: not all the global users are comfortable sharing their views and posts on an open platform where the chances of being abused or bullied horrify them. Secret anonymous social media portal is their answer.
Many people are also aware of the sad ending of these applications when cyberbullying became a significant issue that could not help the app to sustain for a longer time. However, failures of such applications do not change the face of anonymous social media applications that are doing great in the market right now, such as Whisper and Anomo with crucial features appreciated by the users.
And if you wish to proceed further to develop anonymous social media applications, let's investigate the same. Here we have carefully curated all the required information for you so that you can go through it and enter the industry with an incredible idea.
What are Anonymous Social Media Applications and its Types
Anonymous social media platform or application is considered to be a safer place, especially to those users that prefer to keep their views to a private world. Such applications ensure secure privacy over the content without being bullied on the social media platform.
Anonymous social media networks are of two types:
- Anonymous Social Media Platform: At this portal, users can share their content through the news feed.
- Chat-based Social App: This platform includes group messaging portal or one-to-one chat rooms where users can communicate without disclosing their identity.
If you blend both the types, users can register directly for Anonymous social media applications to share their news feeds as well as talk to other users or groups on a single platform.
How to Share Content and Interactions in Anonymous Applications?
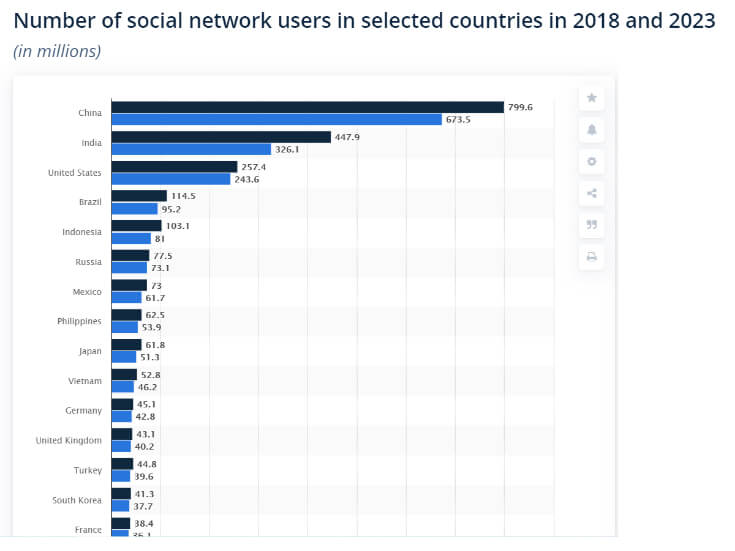
The major goal of anonymous social networking applications, other than privacy, is to serve decent communication. As a matter of fact, most social network users are most found in China, according to statista. Some of the users from the list are the testers or bullies creating fake and untrusted accounts that must be monitored to reduce cyberbullying.
The anonymous social media application also serves the main feature of private chats which is based on the 'one-to-many' sharing model. To pull out such a request, developers have to continually work upon user engagement, maintaining high-level quality and security. For a similar purpose, developers need to make sure that users are connected through a geographical location, or they belong to a specific community.
In order to do so, developers have to make sure of the following feeds while developing anonymous social applications:
- Latest Feeds: This feed helps in tracking all the recent posts of the users to fill the popularity feed as quickly as possible.
- Explore feeds: This feed serves the popularity of recent posts, including shared posts with the most significant number of comments and likes.
- Corporate Feeds: Such anonymous social applications are also logged in by businesses and companies. For such accounts this feed enables users to unite with others similarly, as LinkedIn.
- School Feeds: This feed will help the user to add more list of schools from the database with additional search features.
- Geolocation Feeds: This feed enables tracking of the location that displays posts from the user which are in the nearby place.
How will Technology Help Users to Avoid Cyberbullying?
An application like Whisper taught us that such social media posts can be anonymous and can be used for a long time without being a victim of a verbal user on the platform. Let's understand how technology can help in reducing cyberbullying on such applications. it can help you save yourself and your platform from cybercrime.
Suppressing bullies by tracking users
Such an application can work only when the users are tracked on a regular basis. Moderators play a significant role during this step to track those users who are not entirely anonymous to the owners of the application. An application must divide the users into different categories of banned, untrusted, and trusted. For instance, a moderator can ban the users if they fail to recognize a character identifier.
Moderating system
Believe it or not, the moderating system plays a vital role in measuring the credibility of the user on this application. Moderators help in processing and curating the post at the same second when it is created. Whisper application, for example, uses Arbiter, which is the company's machine learning tool to identify safe content by using filters.
Help and Support
It is an additional feature which is provided to the users of the application for providing a real-time solution to their issues. For instance, a user posting about their damaged married life is redirected to the other sites. Such sites offer a real-time solution to users. With such help and support features, moderators can identify cyberbullies.
Removing or flagging of posts
In case any user comes across any post or comment which is inappropriate to the readers, users can flag such posts. To an extent, moderators can keep track of such databases and identify the theft or cyberbully trying to malfunction any user's profile or personal information.
Other than the mentioned pointers, being the owner of the application, you can choose what type of data you wish to protect. It is highly suggested that the owner of the application must store as little data as possible in order to protect their privacy and sensitive information. Encrypting the data is highly recommended by providing anonymity for the users within chat boxes with encrypted messages. Activating GPS location feature also helps in serving the login details and device footprint of the user, which can be then tracked by the moderators.
Users, on the other hand, can also use VPN networks which help them to protect them for surveillance. However, the owner of the application must track the systems which are unauthentic as well.
To Conclude
Now, when you are aware of the Do's and Don'ts while developing anonymous social media apps, you must consider the discovery phase as the top priority. The development phase of the product will lay the foundation of your application. It is to ensure how credible and authentic the platform is for users. To sustain the eligible credibility, one must consider functions specifications, visual prototype and interface designing that will give the clear picture of the application. Depending on your technical partner, this phase might take from 2 to 6 weeks to conclude.
Owebest Technologies, which is a leading development company, helps you define a credible scope of work and roadmap of the project. They will also back you up in setting up the realistic budget to plan your resources and MVP well before time. And once right hands conclude the testing, your application will succeed to a good start with a crafted investment pitch for your financial partners.
Just switching to a great idea of anonymous social media application can only be realized into trusted reality when you have the right technical partner with you. Such secret social media applications must be built by the professional team that works not just on monetary commitment, but on a satisfying scale of loyalty. So, you can contact Owebest Technologies, can push the right path to your vision and dream project. After all, creating an application might be a daily task for the developer, but the skilled and passionate technical partners rightly understand the soul and commitment.




















.jpg)
.jpg)
.jpg)
